
Monday, February 26, 2007
Sunday, February 25, 2007
Thursday, February 22, 2007
Quote of the Day
Jim Carrey is one of my favorite comedians, and I find this quote from him to be very interesting.
Source: http://www.timesleader.com/mld/timesleader/entertainment/16746160.htm
Sometimes I sit out in my backyard and I look at the birds. The hummingbirds will come by and whack me in the head and fly away. The bird has no respect for my deed to the land. It’s his property as far as he’s concerned, and that’s just the reality of life. We think that we’re the ones in control but it’s all an illusion.
Source: http://www.timesleader.com/mld/timesleader/entertainment/16746160.htm
Friday, February 16, 2007
Happy TET Everyone!
Vietnamese New Year is just one day away. :)
Hope this new year will bring you and your loved ones prosperity, good health, and the best of luck.
Here is a little fire pig horoscope for you. Check out more horoscope at www.tuvi.info.
Jan 22, 1947 to Feb 9, 1948
Feb 18, 2007 to Feb 6, 2008
Pig people are friends for life. Their relationships are very deep, devoted, and rich beyond measure. The Pig people are noble and give and receive lots of hugs. They are gallant and extend old-fashioned chivalries towards people they meet. Pig People are quiet, studious, and thorough. On the other hand, they have a quick temper and sometimes have to pay for their rash impulsiveness. However, no one can overcome their inner strength; they have such tremendous fortitude and jump the goal post very time. The Pig will have an abundance of good fortune and an abundance of years. The Pig will know a life filled with serenity and riches.
Soup, Oolong Tea, and Candied Ginger are among keys to good health.
Bold and adventurous, the captivating Fire Pig makes a big splash in living technicolor. This Pig is a Big Time Operator who makes things happen through his clever wit and well-rounded talents. They never rest on their laurels because they have an insatiable thirst for power. They know that once they sit still, someone will pass them by. Like the ultimate agricultural expert, Fire Pigs plan, plant the seeds, cultivate, and reap a big harvest, no matter what projects they pursue. They have every right to be proud as punch at having such a successful career and financial status. They can tumble, too -- also big time, but they get right back up and try again. In the Hugs and Kisses Department, let's just say that the Fire Pigs are really quite lucky! It's true that they have to work pretty hard to get something in return, but oh my, don't they receive big dividends. Lucky in love. Lucky in life.
Famous Pig People: Chiang Kai-Shek, Lee Kuan Yew, Kim Dae Jung, Syngman Rhee, Tennessee Williams, Julie Andrews, Albert Schweitzer, Jerry John Rawlings, Prince Rainier, Georges Pompidou, Chuck Yeager, Henry Kissinger, King Fahd
Hope this new year will bring you and your loved ones prosperity, good health, and the best of luck.
Here is a little fire pig horoscope for you. Check out more horoscope at www.tuvi.info.
Jan 22, 1947 to Feb 9, 1948
Feb 18, 2007 to Feb 6, 2008
Pig people are friends for life. Their relationships are very deep, devoted, and rich beyond measure. The Pig people are noble and give and receive lots of hugs. They are gallant and extend old-fashioned chivalries towards people they meet. Pig People are quiet, studious, and thorough. On the other hand, they have a quick temper and sometimes have to pay for their rash impulsiveness. However, no one can overcome their inner strength; they have such tremendous fortitude and jump the goal post very time. The Pig will have an abundance of good fortune and an abundance of years. The Pig will know a life filled with serenity and riches.
Soup, Oolong Tea, and Candied Ginger are among keys to good health.
Bold and adventurous, the captivating Fire Pig makes a big splash in living technicolor. This Pig is a Big Time Operator who makes things happen through his clever wit and well-rounded talents. They never rest on their laurels because they have an insatiable thirst for power. They know that once they sit still, someone will pass them by. Like the ultimate agricultural expert, Fire Pigs plan, plant the seeds, cultivate, and reap a big harvest, no matter what projects they pursue. They have every right to be proud as punch at having such a successful career and financial status. They can tumble, too -- also big time, but they get right back up and try again. In the Hugs and Kisses Department, let's just say that the Fire Pigs are really quite lucky! It's true that they have to work pretty hard to get something in return, but oh my, don't they receive big dividends. Lucky in love. Lucky in life.
Famous Pig People: Chiang Kai-Shek, Lee Kuan Yew, Kim Dae Jung, Syngman Rhee, Tennessee Williams, Julie Andrews, Albert Schweitzer, Jerry John Rawlings, Prince Rainier, Georges Pompidou, Chuck Yeager, Henry Kissinger, King Fahd
Thursday, February 15, 2007
Some Interesting Gifts From Microsoft
Microsoft's Gift to Netscape

Microsoft's Gift to the Mozilla team for delivering Firefox

Microsoft's Gift to Apple

Disclaimer: I have collected these photos from different websites that I visited, but I have forgotten their URLs. I found them to be interesting and so I'm sharing with you.

Microsoft's Gift to the Mozilla team for delivering Firefox

Microsoft's Gift to Apple

Disclaimer: I have collected these photos from different websites that I visited, but I have forgotten their URLs. I found them to be interesting and so I'm sharing with you.
Wednesday, February 14, 2007
SSL Handshake Protocol
Phase 1: Establish security capabilities
Phase 2: Server authentication and key exchange
Phase 3: Client authentication and key exchange
Phase 4: Finish
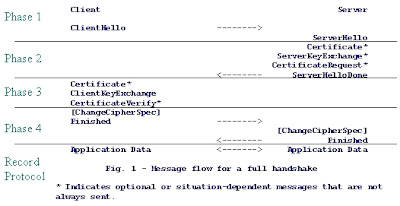
Phase 2: Server authentication and key exchange
Phase 3: Client authentication and key exchange
Phase 4: Finish

Thursday, February 8, 2007
YouTube is My American Idol
Here's a selected list of early YouTube investors and what their investment is now worth based on Google's stock price as of Wednesday:
Chad Hurley, YouTube co-founder, 694,087 shares*, $326 million
Steve Chen, YouTube co-founder, 625,366 shares*, $294 million
Harvard University, 37,866 shares, $17.8 million
San Francisco Symphony, 1,700 shares, $800,000
Maury Povich, television talk show host, 170 shares, $79,900
*Does not include shares held in trusts
Source: www.sfgate.com
Chad Hurley, YouTube co-founder, 694,087 shares*, $326 million
Steve Chen, YouTube co-founder, 625,366 shares*, $294 million
Harvard University, 37,866 shares, $17.8 million
San Francisco Symphony, 1,700 shares, $800,000
Maury Povich, television talk show host, 170 shares, $79,900
*Does not include shares held in trusts
Source: www.sfgate.com
Tuesday, February 6, 2007
Encryption Techniques
This semester, I'm taking ISA 662, Intro to Information Security, and here are some of the encryption techniques we discuss in class.
- Blind Signatures
- Blind signatures are used in situations where an author wants to get his or her message signed by a third party without revealing any information about the message to this party. They have many uses including timestamping, anonymous access control, digital cash, and cryptographic election systems. Blind signature schemes were first introduced by David Chaum using RSA signatures.
- Identity-based Encryption
- Identity-based encryption is a key authentication system that uses a public and private keys pair. It is called identity-based encryption, because the public key is some unique information about the identity of the user, such as his or her email address, and the system requires a trusted third party called Private Key Generator or PKG to generate the private key for the user based on the user’s unique value or public key.
- Threshold Cryptography
- Threshold Cryptography enables a private RSA key to be shared among K individuals called shareholders that are engaged in encryption or decryption, such that any K-1 or K-2 of them can decrypt incoming messages without reconstructing the key. The objective of Threshold Cryptography is to implement a distributed architecture in a hostile environment. It can be implemented to redundantly split the message into n pieces such that with t or more pieces the original message can be recovered.
- Key Escrow
- Key escrow is the arrangement where the user’s private key is generated and held in escrow by a trusted third party so that this key can be later used by a government agency to decrypt suspicious messages. Key escrow is used in identity-based encryption. The Private Key Generator or PKG generates and holds in escrow the private key it helps generate based on the user’s unique characteristic.
- Side Channel Analysis
- Side Channel Analysis helps assure the effectiveness of measures taken to protect cryptographic devices from leaking secret information. Attackers can take advantage of this secret information, which is gained from the physical implementation of a cryptosystem, rather than theoretical weaknesses in the encryption algorithms. This type of attack is known as side channel attack, which uses the extra source of information, such as timing information, power consumption, electromagnetic leaks or even sound to break the system.
Subscribe to:
Posts (Atom)
